Table of Contents
Introduction
Macbooks are chatty things. macOS has many peer-to-peer networking protocols that are on by default that a user is not completely aware of. This article aims to document some ways to make a Macbook more trustworthy when, for example, you're preparing to take it to an international hacking conference like 38C3.
I'm using an M1 MBP on Sequoia 15.1.1.
Expectations, Goals, and Presumptions
In order to reduce the overall attack surface of a Macbook from potentially malicious actors in my immediate vicinity, I need to turn off all of the Macbook's wireless communications. Internet access is critical, especially when hacking on projects with old friends and new friends at a place like CCC. The goal then is to use a USB-C cable to connect my iPhone for 5G access. While iPhones are also chatty devices, modern iOS devices are significantly more secure compared to macOS.
People within radio frequency distance of my Apple devices are not my only threat. I also have to be concerned with nation-state threat actors targeting the conference. It's in my best interest for my iPhone and my Macbook to be employing a Wireguard VPN to protect my outbound internet traffic. Wiregaurd must use a pre-shared key and the egress server should be in a non-FVEY state.
Directions
The following directions are only based on my experiences as s security engineer. If you have recommendations, please reach out!
Lockdown Mode
Assure that Lockdown Mode is enabled.
Alternatively, assure that new accessories must be approved to connect.
Lockdown Mode on iOS is also important. LDM disables 2G connectivity by default. Further, you should configure your cellular SIM/eSIM settings to "5G On" (under Voice & Data) instead of 5G Auto or 4G. This may help mitigate some IMSI-catcher style downgrade attacks, but it will not prevent them.
GrapheneOS has even better controls.
Apple Wireless Direct Link
AWDL (Apple Wireless Direct Link) is used for peer-to-peer connections that support AirDrop, AirPlay, and other Apple ecosystem features. Even if I'm not actively using AirDrop, the "awdl0" interface is a core part of the OS’s networking stack.
ifconfig
awdl0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500
options=6460<TSO4,TSO6,CHANNEL_IO,PARTIAL_CSUM,ZEROINVERT_CSUM>
....
media: autoselect
status: active
sudo ifconfig awdl0 down
awdl0: flags=8822<BROADCAST,SMART,SIMPLEX,MULTICAST> mtu 1500
options=6460<TSO4,TSO6,CHANNEL_IO,PARTIAL_CSUM,ZEROINVERT_CSUM>
....
media: autoselect (<unknown type>)
status: inactive
This will not persist after a system reboot.
Wi-Fi
Disabling Wi-Fi can be performed in terminal:
en0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500
options=6460<TSO4,TSO6,CHANNEL_IO,PARTIAL_CSUM,ZEROINVERT_CSUM>
....
media: autoselect
status: active
networksetup -setairportpower en0 off
en0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500
options=6460<TSO4,TSO6,CHANNEL_IO,PARTIAL_CSUM,ZEROINVERT_CSUM>
....
media: autoselect
status: inactive
Bluetooth
Disabling Bluetooth is as simple as toggling it in the macOS taskbar.
Via terminal/Brew, you may also use blueutil:
brew install blueutil
See if on (1) or off (0)
blueutil -p
0
Or set it:
blueutil -p 0
Misc. Network Devices
There are miscellaneous network devices listed in macOS's network settings.
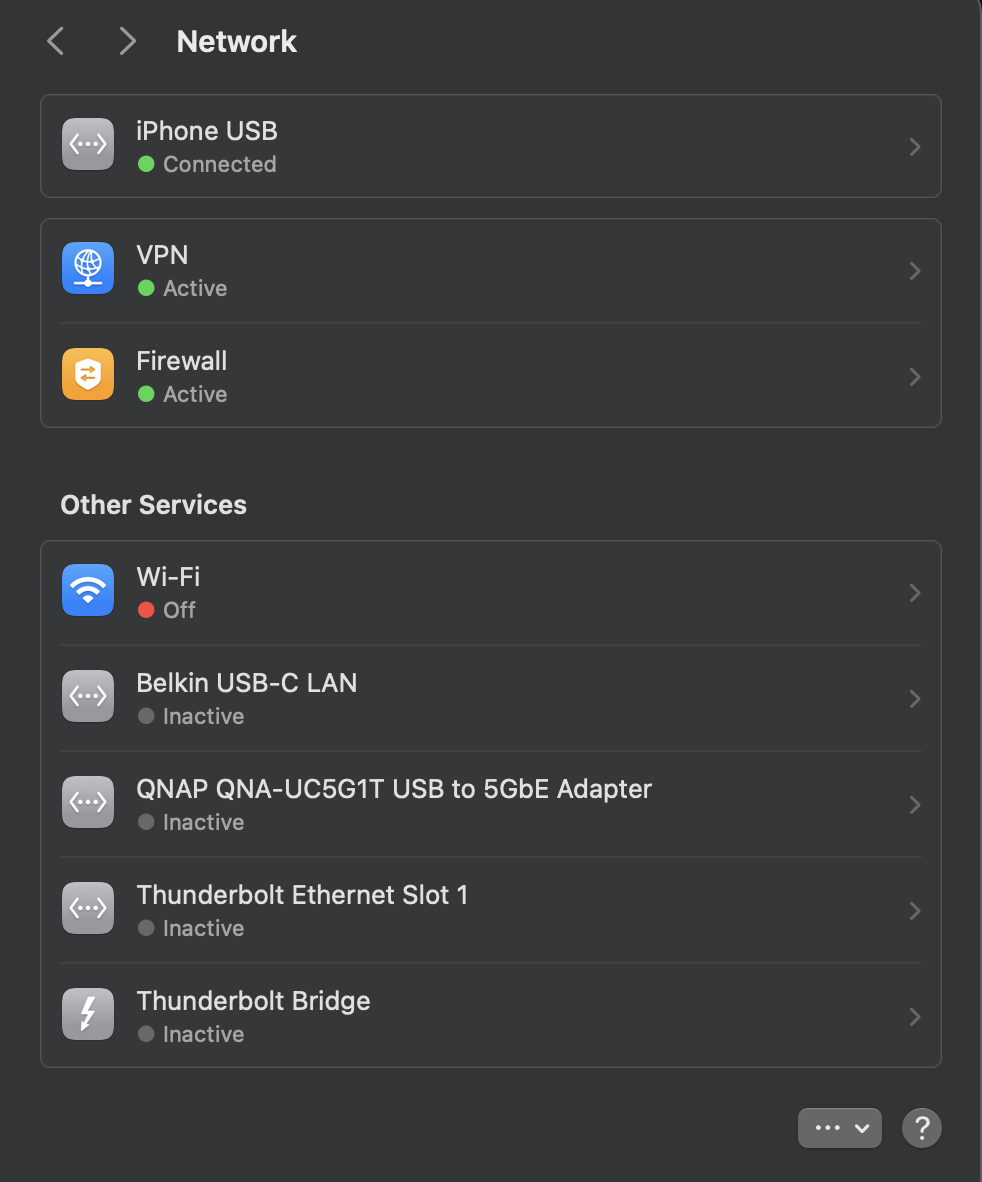
I went into each one and clicked "Make Inactive".
Additionally, if you want to understand which logical devices are tied to these hardware devices, you can use:
networksetup -listallhardwareports
However, this command doesn't report its status such as Active or Inactive. I'm not aware of a terminal command to do this. "ifconfig" could be cross-referenced to see which of those devices is active or inactive.
Firewall
Assure that the macOS firewall is enabled and that, under options, it is set to "Block all incoming connections."