Please be warned this is from 2012 and is kept for historical value.
To update on my short experience as a Tor node operator, It’s been over a week now and in that week I made some changes.
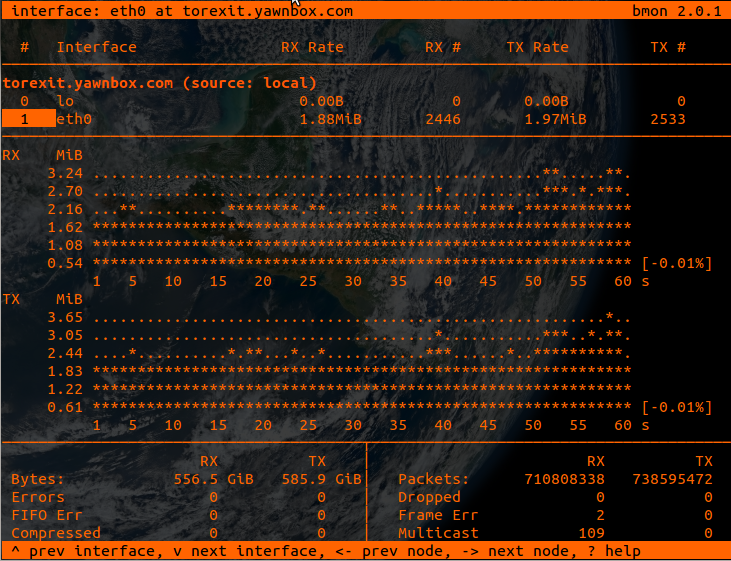
First and foremost, since I’ve been online for a few days straight, I’ve been flagged by the Tor network as a “Stable” node. So now I’m processing traffic rather consistently. I’ve also been flagged as a “Guard“, meaning,”…each Tor client selects a few relays at random to use as entry points, and uses only those relays for her first hop”. More can be read about Guards here.
Secondly, I adjusted (increasing) how much of my bandwidth I’m willing to let Tor use.
RelayBandwidthRate 6000 KB
RelayBandwidthBurst 7500 KB
I’ve observed traffic peaks of 5 Megabytes a second, sending and receiving. This last Friday I noticed that I was passing a lot of traffic. It made me wonder if people are using Tor a lot more on Fridays.
As you can see, 8 Day(s), 19 Hour(s) in I’ve already relayed 1142.4 GiB.
Thirdly, I put up the standard “This is a Tor Exit Router” page on torexit.yawnbox.com.
Lastly, I am now allowing port 443 to pass HTTPS traffic. So here’s my updated Reduced Exit Policy:
ExitPolicy accept *:119 # accept nntp as well as default exit policy
ExitPolicy accept *:22 # ssh
ExitPolicy accept *:443 # https (HTTP via TLS)
ExitPolicy accept *:465 # smtps (SMTP over SSL)
ExitPolicy accept *:993 # imaps (IMAP over SSL)
ExitPolicy accept *:994 # ircs (IRC over SSL)
ExitPolicy accept *:995 # pop3s (POP3 over SSL)
ExitPolicy reject *:* # no exits allowed
It turns out that in order to be flagged as an exit, the node needs to either be exiting ports 443 and 80 or 443 and 6667. And I’m being stubborn about only passing, ideally, encrypted traffic. However, not having the check-mark next to “Exit” on my Network Status page doesn’t mean that I’m not an exit– the Tor network certainly knows I’m exiting.
Props to everyone at the UW/Tor hack-fest. Absolutely brilliant people having the most interesting of conversations. I really enjoyed the two days I spent around them, soaking in as much as I could. It made me think critically about a number of problems that I hope to blog about soon.
Node Operator Notes
Reloading Tor instead of restarting it (the service) allows me to update my torrc file without disrupting traffic.
sudo /etc/init.d/tor reload
Also, I added two security features to help block annoying attacks. Make sure you’re familiar with how to use them.
sudo apt-get install -y fail2ban denyhosts