Table of Contents
- Related Articles
- Introduction
- If you're not using Tor you're doing it wrong
- HTTP / Postcard
- HTTPS / letter
- Virtual Private Network (VPN): a 1-hop proxy
- VPN / postcard
- VPN / letter
- VPN circuits
- The onion router: a 3-hop proxy
- Tor / postcard
- Tor / letter
- Tor circuits
- Ads vs. NSA
- VPN behavior
- Tor behavior
- Onion services
- Onion services behavior
- Tor browser
- Onion services hosting
- Tor applications
- Questions and feedback
Related Articles
In my Setting up a Wireguard VPN with DNS ad blocking article, I discuss some more advanced issues with VPNs along with some possible mitigations.
Introduction
Techno-Activism Third Mondays (TA3M) is a meetup I helped coordinate in Seattle and occasionally presented in.
Techno-Activism Third Mondays (TA3M) are informal meetups that occur on the same date in many cities worldwide. It is designed to connect techno-activists and hacktivists who work on or with circumvention tools, and/or are interested in anti-censorship and anti-surveillance technology. Currently, TA3M are held in New York, Washington, DC, Amsterdam, Portland, Tokyo, and more.
This presentation was given at the University of Washington on January 18, 2016 and the original slide deck is available on Google Docs.
This presentation is geared toward helping people understand some basics about VPNs and Tor.
Please remember 2016: there were still many very slow adopters of basic HTTPS on mainstream websites. That's why one slide below says things like "http://bbc.co.uk" and not "https://bbc.co.uk" -- because I'm explaining the differences between a HTTP connection without TLS encryption, and one with TLS encryption. Today, in 2024, thankfully, the BBC uses HTTPS.
Two interesting facts about this presentation:
At the time, in January 2016, I was an intern at the ACLU of Washington, consulting on their communication practices, and helping deploy SecureDrop for secure and anonymous legal intake.
A former Executive Director of The Tor Project was in the audience of this TA3M, and they later approached me to offer me a job as their full-time Grant Writer.
If you're not using Tor you're doing it wrong

This quote is from a November 2015 interview of Edward Snowden by Micah Lee in Moscow titled, "Edward Snowden Explains How To Reclaim Your Privacy".
This talk is for everyone. You don’t need to be an activist, journalist or a lawyer to need Tor. Even the most boring, uninteresting person in the world should be defending their right to privacy and freedom of expression by using Tor.
The aim of this ~30 minute talk (plus Q/A) is to help make it easier for people to understand Tor and Onion Services. It is not a highly technical talk, but it is technical. I expect that users that wish to gain knowledge of how technical systems work, to take advantage of them, must learn some basic technical material.
My talk discusses how the Tor network works to protect your privacy by juxtaposing plain HTTP, HTTPS, and also mainstream VPN technology. I will be discussing why the advertising industry is an even greater threat than even the NSA to most people, and why VPNs just can’t cut it. Lastly, I will discuss how Onion services is a paradigm shift from standard client-server communications, how it works to protect your privacy, and why Onion services is an important application for service providers concerned about uptime and security.
HTTP / Postcard
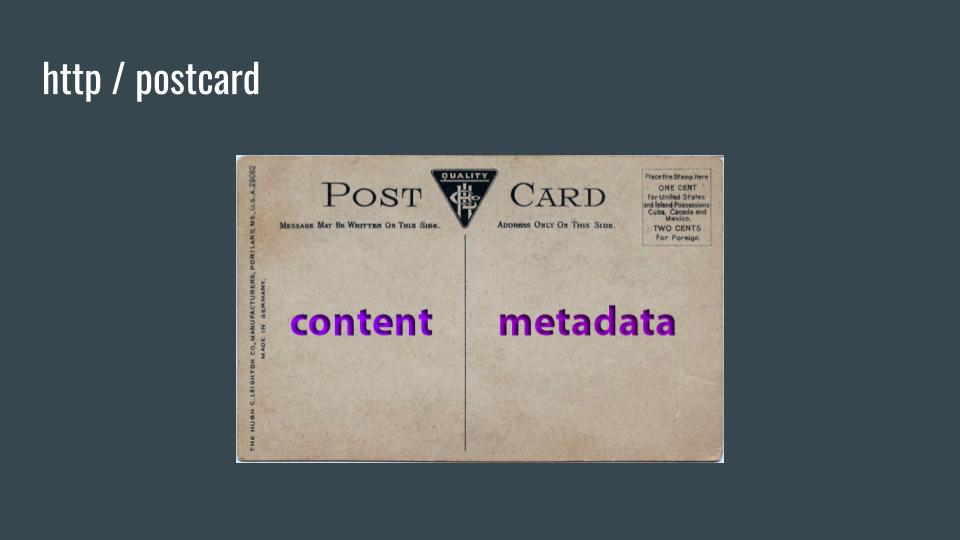
Sending a postcard in the mail allows anyone that handles the postcard to view and retain both the metadata:
- who
- what
- where
- when
and any content:
- personal messages to the receiver
Plain HTTP over the internet is no different, except that digital content is much easier and cheaper to collect and store.

This clear-text content and metadata is represented here in purple. It is completely defenseless in transit. Anyone connecting to http://bbc.co.uk allows any network operator between you and the BBC service provider to view, retain, and maybe even change the metadata or content in transit.
HTTPS / letter
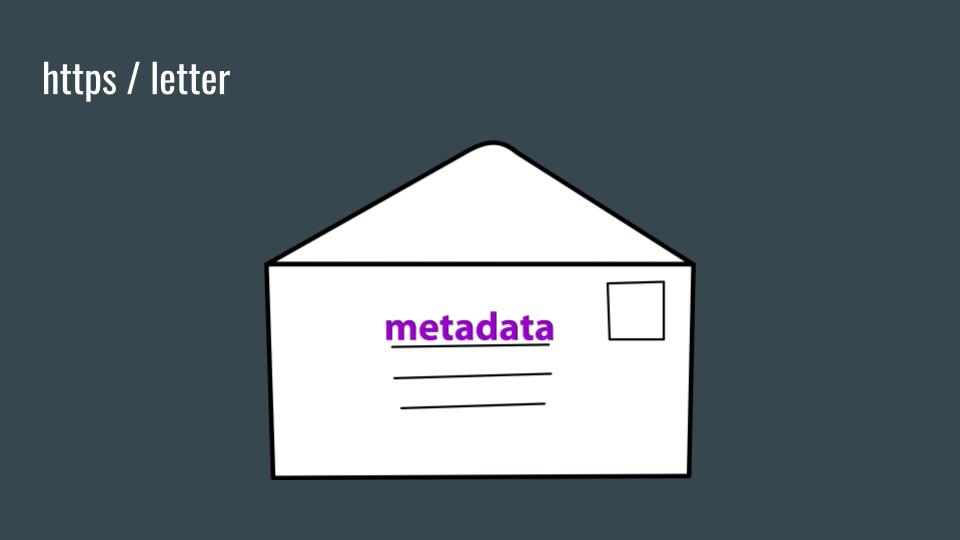
Sending a letter in the mail has one layer of protection, the envelope, and is analogous to HTTPS. The NSA considers HTTPS encrypted traffic “clear text” because metadata is still clear text, and a lot can be learned about the content of HTTPS encrypted traffic through automated analysis. NSA can also make assumptions about what content is in the TLS-encrypted data with captured HTTPS traffic.
HTTPS is two different protocols: HTTP + TLS. TLS is basically a encrypted tunnel for HTTP traffic to go through. Combined, it's called HTTPS.
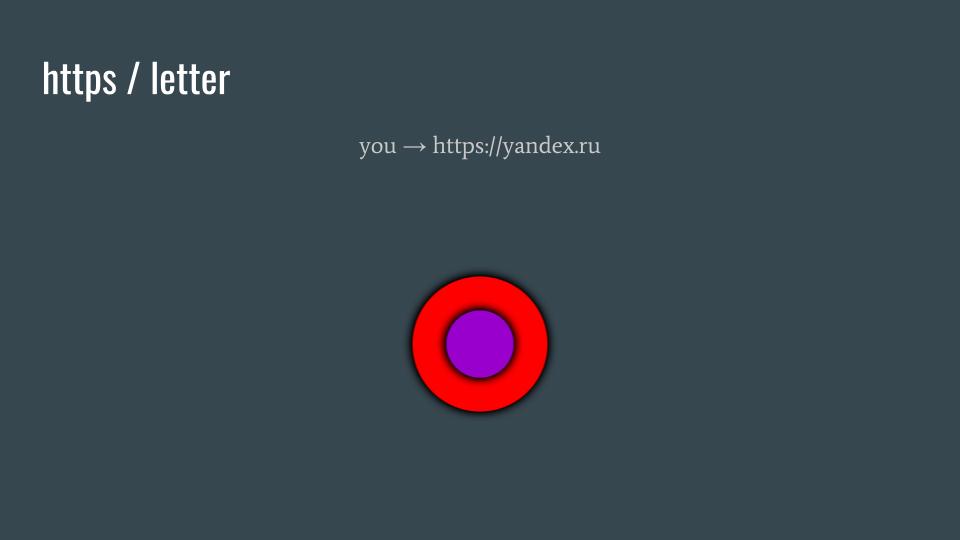
HTTPS protected content is represented here by a red circle protecting the purple content at the center. Connecting to https://yandex.ru--even though encrypted with TLS--still divulges a great deal of information (metadata) to anyone handling your traffic as it traverses the Internet.
Virtual Private Network (VPN): a 1-hop proxy

VPNs are typically one-hop proxies. It is possible to set up your own multi-hop VPN proxy, just like you can set up your own private Tor network if you have the time, expertise, and money. But mainstream VPN providers, to keep the time it takes to send your traffic back and forth across the Internet, only use one proxy. In other words, VPN providers, to keep most people happy, focus on speed rather than privacy.
Purchasing a private mailbox (PO Box, etc) from a UPS store is analogous to purchasing VPN service from a provider. You are paying someone to “one-hop” proxy your mail so that the destination of your mail cannot know your real home address.
VPN / postcard
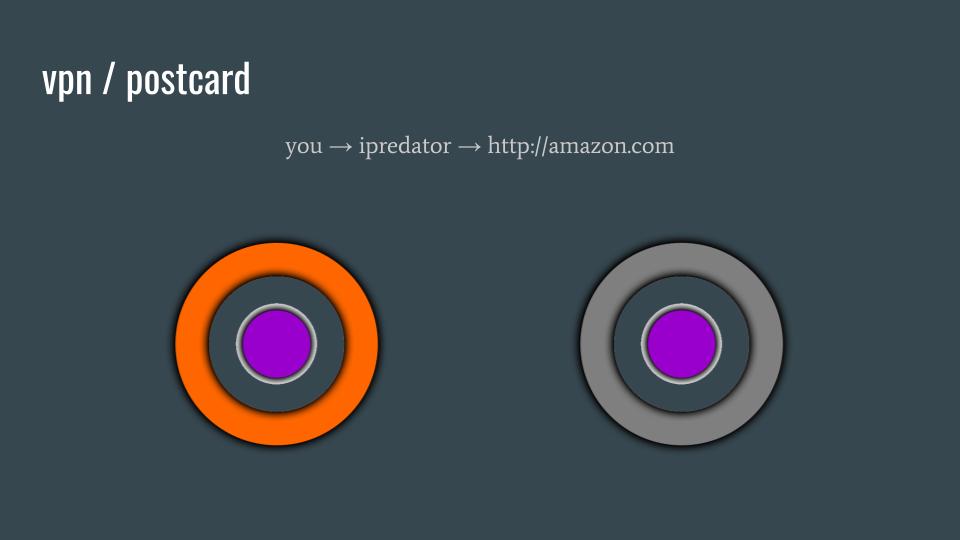
In this example, you are using the Ipredator (ipredator.se) VPN service provider in order to connect to http://amazon.com. (2016) Amazon still does not provide transport security and thus content privacy for users of their service when searching for products to buy. Your Amazon-bound Internet traffic has one layer of protection, the orange circle, only up until the VPN service provider. Once your Amazon-bound traffic leaves the VPN provider (the one-and-only one-hop proxy), Amazon searches are as naked as postcards to the people handling that internet traffic.
If network adversaries, observing your Amazon searches somewhere between the VPN provider and Amazon, may also be able to determine who is doing the searches based on the content of the internet traffic. These Amazon searches are just like sending postcards in the mail. Said adversaries can view, record, and change any of the metadata or content.
VPN / letter

In this example, when connecting to https://wikipedia.org and using the Ipredator VPN service, the data (purple) is protected by by a layer of TLS (red) and also the VPN (orange). Once the Wikipedia-bound internet traffic is proxied by Ipredator, it loses the VPN-encrypted (orange) layer, and your traffic’s content is still protected by Wikipedia’s TLS-encrypted (red) layer.
VPN circuits

Remember, VPNs are one-hop proxies. The “circuit” that is made between you and the VPN service provider is static — the operator and the IP network (called an IP subnet) never changes. The “IP subnet” of the VPN provider determines the IP address that your Internet traffic uses and is constrained by the pool of available IP addresses the VPN provider has available.
For example: If your home network has 192.168.1.0/24 assigned for all of the computers in your house, then any computer in your network can only ever be 192.168.1.2 - 192.168.1.254. I don't want to get into the details of IP subnetting, I just want to be clear about how there are only 253 usable IP addresses in that IP subnet, .2 - .254. All VPN providers on Earth have limited IP networks.
The one-hop proxy circuit design is purposeful in order to maintain minimal latency (the time it takes for your traffic to reach the VPN provider), and to maximize bandwidth (how much you can download or upload per second).
The onion router: a 3-hop proxy
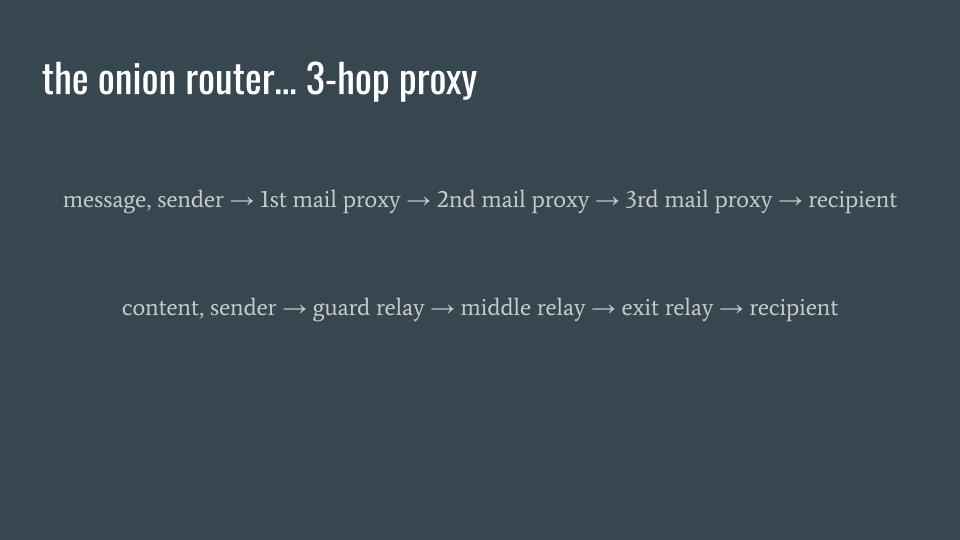
Tor is more complex and can generally be described as a three-hop proxy when someone is using Tor Browser to connect to a normal website. It would be like purchasing PO BOX services from three different, globally diverse mail proxy service providers, and each of those providers automatically works with each other to relay your mail to maximally protect your home address and maybe even your identity.
When sending mail communications:
- the first mail proxy knows who you are and also knows who the second mail proxy is.
- The second mail proxy only knows who the first and third mail proxies are.
- By the time your mail gets to the third and final mail proxy, your home address is not in any of the metadata that is destined for the recipient.
Unless you disclosed your identity in the content of your communications, the recipient cannot know your identity, either.
Tor / postcard
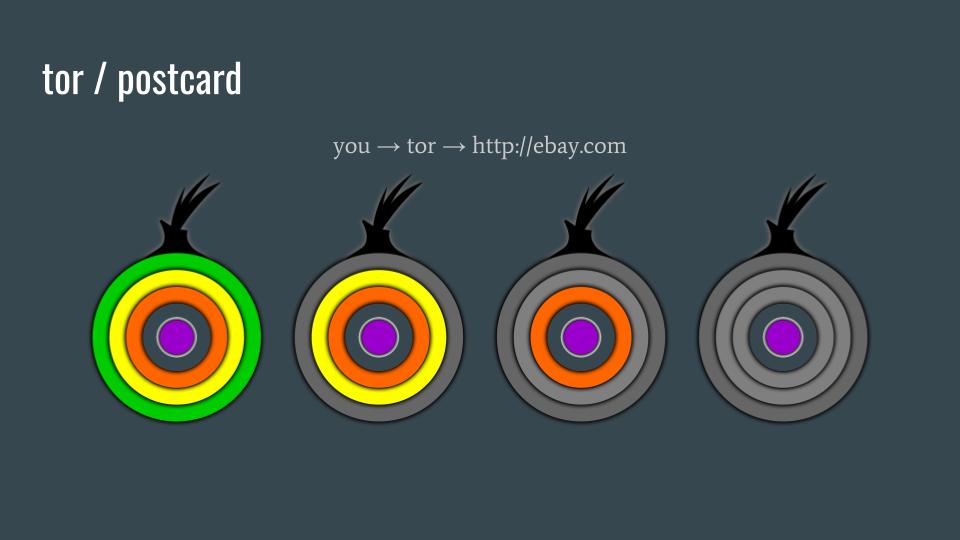
Now let's look at an example of talking to (2016) http://ebay.com with Tor Browser.
Tor encrypts your Ebay-destined traffic in three layers before leaving your computer.
Green circle: the Tor encrypted traffic from your computer to the Tor guard relay. The guard relay removes this first layer of encryption.
Yellow circle: the Tor encrypted traffic from the guard relay to the middle relay. The middle relay removes the second layer of encryption.
Orange circle: the Tor encrypted traffic from the middle relay to the exit relay. The exit relay removes the last layer of encryption and sends your traffic on to Ebay. Naked.
Connecting to http://ebay.com over Tor and searching Ebay does not disclose your IP address or your identity unless you log in to Ebay. Logging in to Ebay would disclose your identity to Ebay and thus may disclose the probability of your physical location if you gave Ebay or PayPal your home address as a shipping destination. If you browse Ebay without logging in but search for things that could allow an adversary to identify who is doing the searches, then you may disclose your identity that way, too.
If network adversaries observing the Ebay searches somewhere between the Tor exit relay and Ebay may also be able to determine who is doing the searches based on the content of the Internet traffic, because these Ebay searches are just like sending postcards in the mail. Said adversaries can view, record, and change any of the metadata or content.
Tor / letter
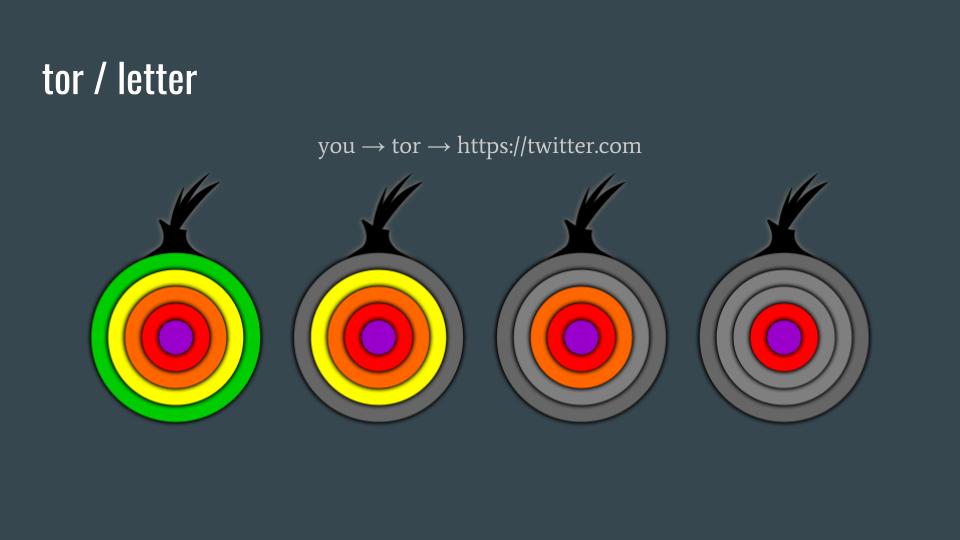
Now let's look at an example of talking to (2016) https://twitter.com with Tor Browser.
Tor encrypts your Twitter-destined traffic in three layers before leaving your computer. Then, because Twitter requires that you use HTTPS to connect to Twitter, the first connection to Twitter establishes TLS (red), and then all of your Twitter-bound traffic will be encrypted in four layers of encryption.
Green circle: the Tor encrypted traffic from your computer to the Tor guard relay. The guard relay removes this first layer of encryption.
Yellow circle: the Tor encrypted traffic from the guard relay to the middle relay. The middle relay removes the second layer of encryption.
Orange circle: the Tor encrypted traffic from the middle relay to the exit relay. The exit relay removes the last layer of encryption and sends your traffic on to Twitter. Because of HTTPS, the content of your Twitter-bound traffic is still protected.
Connecting to https://twitter.com over Tor and searching Twitter does not disclose your IP address or your identity unless you log in to Twitter. Logging in to Twitter would disclose your identity to Twitter. If you browse Twitter without logging in but search for things that could allow an adversary to identify who is doing the searches, then you may disclose your identity that way, too.
Network adversaries observing Twitter searches somewhere between the Tor exit relay and Twitter can not determine who is doing the searches, because these searches are like letters in the mail. Said adversaries can still view and record any of the metadata but not the content.
Tor circuits

Unlike VPN circuits, Tor circuits are generated randomly by your local Tor client. In addition to Tor circuit randomness when starting Tor Browser, circuits are automatically and randomly changed every 10 minutes. Another feature of Tor Browser is that opening a new tab will generate a new circuit for that tab.
The downsides of using Tor is that, due to the required use of three (probably) geographically diverse hops, each of which likely has limited bandwidth, a high-latency and low-bandwidth experience is possible.
This is more of a positive than a negative, especially versus a typical VPN, but a Tor user must trust a random selection of roughly 2,000 guard relay operators and roughly 1,000 exit relay operators per circuit. Further, the Tor specification requires that relays belonging to the same operator cannot be used within the same circuit, presuming any given volunteer operator is not using significantly different (/16) IP subnets.
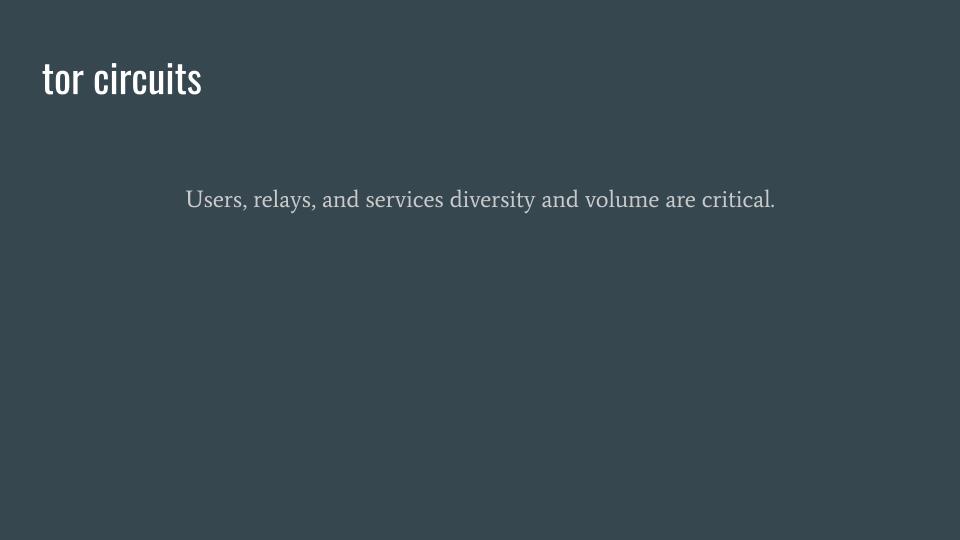
By now, it should be clear that the number of relay operators is critical to the success of Tor and its users. Similarly, because all Tor traffic generally looks the same, it is similarly critical for the success of the Tor network for there to be a high number of users and services, including Onion services.
Most purchasable Internet security services are built using a controlled set of infrastructure. This is a form of centralization. Tor is powerful exclusively because of the decentralized nature of the Tor network and the requirements of the Tor protocol. No other centralized security service can come close to having all of the security and privacy properties as Tor.
Ads vs. NSA
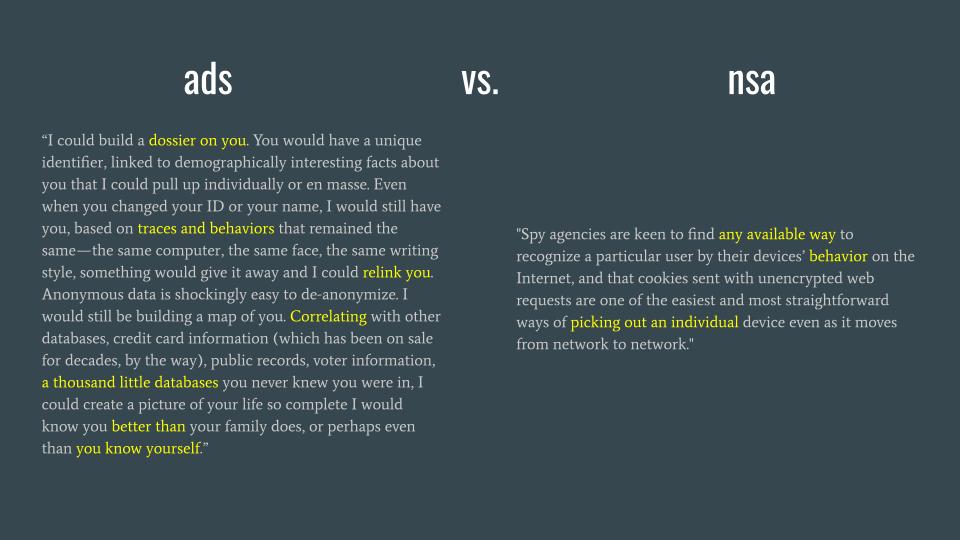
We know that there are two active and constant threats to the internet and thus to its users: governments with intelligence agencies that are bent on the presumption that mass surveillance is valuable, and advertising agencies that are bent on collecting as much information about people as possible in order to control them and sell them products. It just so happens that intelligence agencies are leveraging the work of advertising agencies because of their already deep integration into the large majority of the public internet. Thus, the biggest threat to any internet user is being attacked by advertising agencies.
However, we know that the NSA and FVEY (Five Eyes) focuses on traffic analysis leaving the Tor network, so it is highly probable that the same focus occurs for IP subnets associated with VPN service providers.
Sources:
VPN behavior
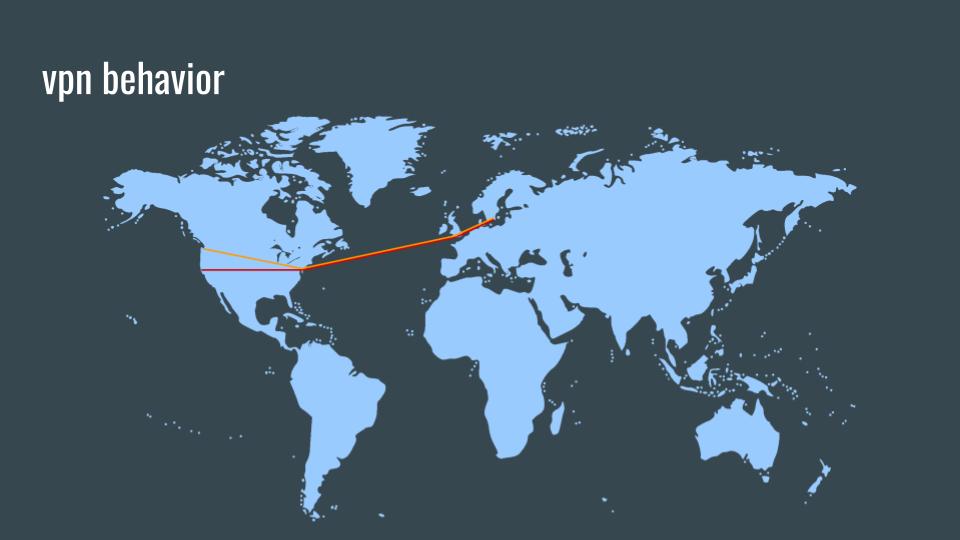
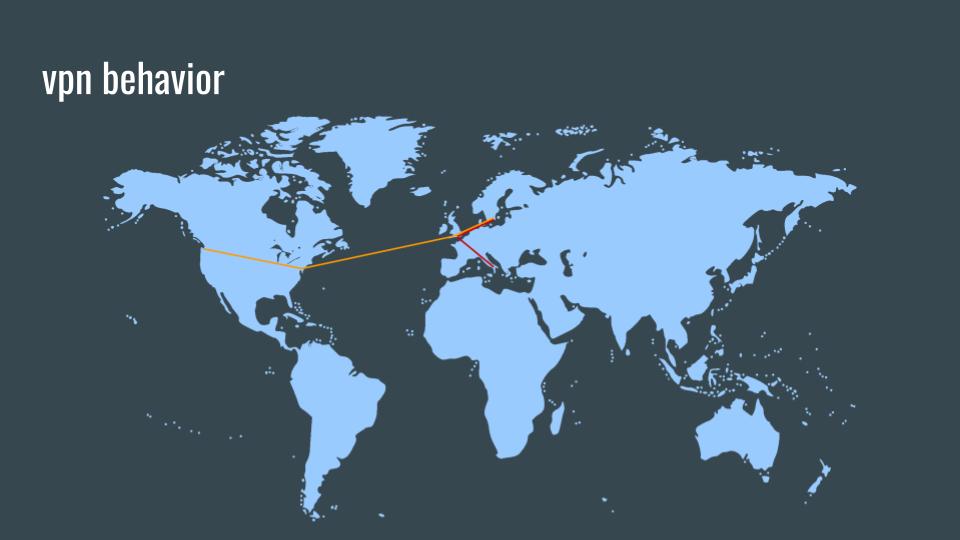
These are examples of two connections to two random Internet services via a one-hop proxy in Sweden. It should be obvious how simple this is and how trivial it would be for a global passive adversary (GPA) to track low-latency, one-hop proxy connections.
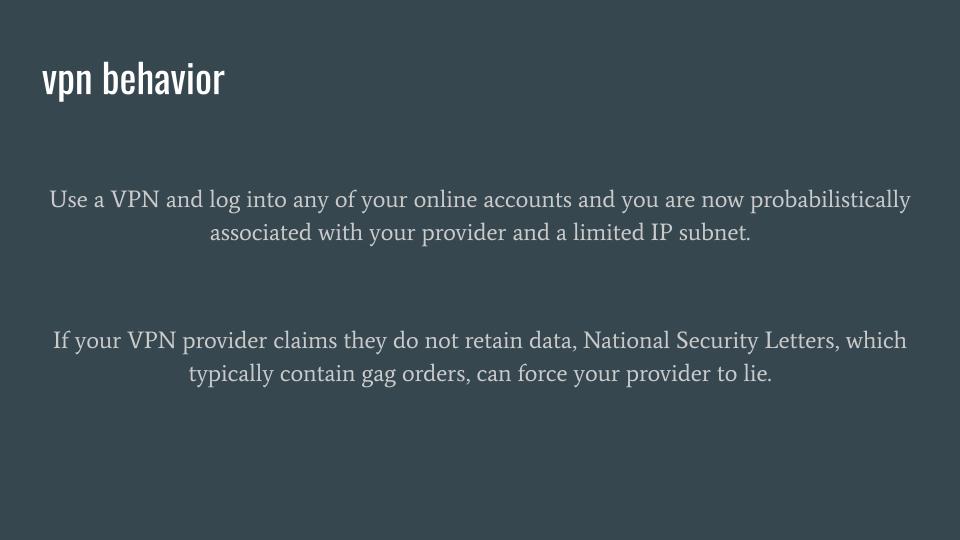
VPN services might feel safe. Especially when you pull out your credit card, you expect to get what you think you’re buying. But its largely false if your goal is to defend personal privacy. VPNs can still be really powerful for getting around censorship, sometimes. VPNs are also still really powerful for file sharing. But both advertising agencies and intelligence agencies are not slowed by technologies that are trivial to undermine with automatic network and data analysis.
Also important to understand is that when you hire one corporate entity to safeguard your privacy, you create one target for an adversary to legally or technically attack. Nobody can assure that VPN services do not maintain connection logs; we know that they are required to maintain payment logs, and we know that some service providers have handed over connection information while also advertising that they do not store connection information.
Tor behavior
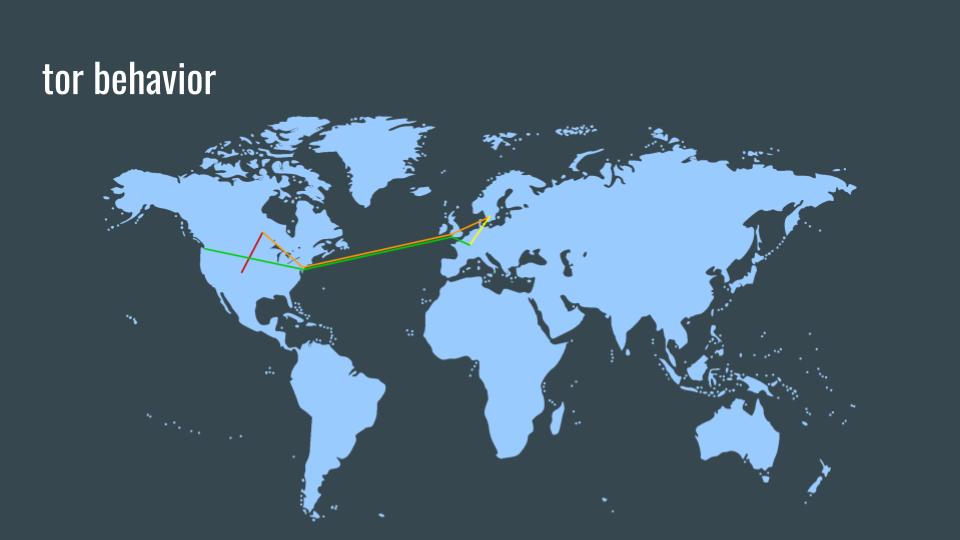
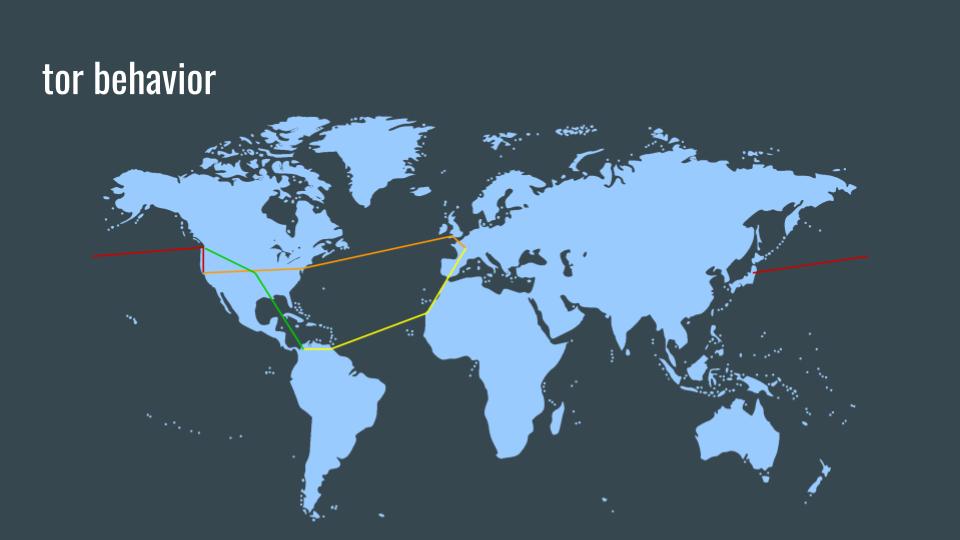
These examples of two Tor circuits demonstrates why adding complexity to network connections is valuable, especially compared to standard options (HTTP, HTTP+TLS, or VPN).
These examples above are also extremely simplified. Because all Tor traffic, no matter if its first-hop, second-hop, third-hop, or onion services traffic, all of those parts of a circuit look identical to a GPA. All Tor relays, especially really big relays, are handling thousands to hundreds of thousands of Tor circuits every second, and the Tor protocol keeps them all looking identical.
I included this slide again to further stress the importance of diversity of the Tor network.
The more Tor users, the more Tor relays, the more Tor services there are, the more any one person blends into all of those things.
Onion services
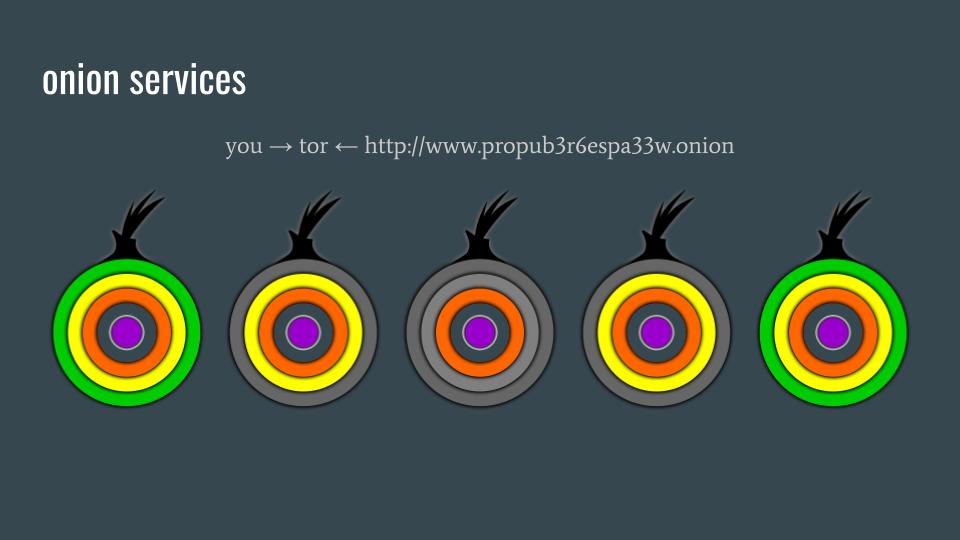
Common client-server connections means that you are making a network request to a server, to see if that server is available, and to request digital resources if the server is available. This is done by communicating directly with the server. Onion services work differently.
Onion services, like the (2016) ProPublica Onion site, is like a permanent Tor user that is constantly connected to the Tor network. You, the client, and ProPublica, the server, both inform the Tor network of your hidden identities. The only difference is that you, the client, makes an anonymous request to the Tor network to ask if the ProPublica server is available. The Tor network, automatically and anonymously, connects the two of you through a random rendezvous point inside the Tor network, in the middle of you and the server. You never actually talk directly to the ProPublica Onion site, and you both have your own three-hops to protect your IP address. Since none of this traffic ever leaves the Tor network, Onion services are not vulnerable to standard forms of passive internet surveillance.

In addition to being free of passive internet surveillance of normal HTTP or HTTPS traffic, Onion services have meaningful security properties that are built into the Tor protocol.
It is important for security to be the default in systems that should be secure. It is also important to empower users by offering a diversity of security properties, automatically and transparently, so that users cannot mess anything up. It is impossible for any one organization to fully grasp each threat model for every one of their users; therefore, security and privacy should be built into the protocol, not options to be enabled if understood.
Aside from the obvious security benefits of Onion services for users, there are obvious security benefits for large organizations. For example, many companies commonly have website or other services outages because of problems with DNS (domain name system), BGP (border gateway protocol), or their CA (certificate authority). Providing Onion services, even as a backup access solution, helps mitigate losing access to Web resources because of these failure points.
The quote on slide 24 is from Roger Dingledine as stated in his 32C3 talk, “Tor Onion Services: More Useful Than You Think”. It is a very informative talk and covers deeper issues, problems, and opportunities for the future of Onion services.
Every “State of the Onion” presentation is worth watching and would be an excellent primer into understanding the nature of Tor and the quality of the people behind it.
Onion services behavior
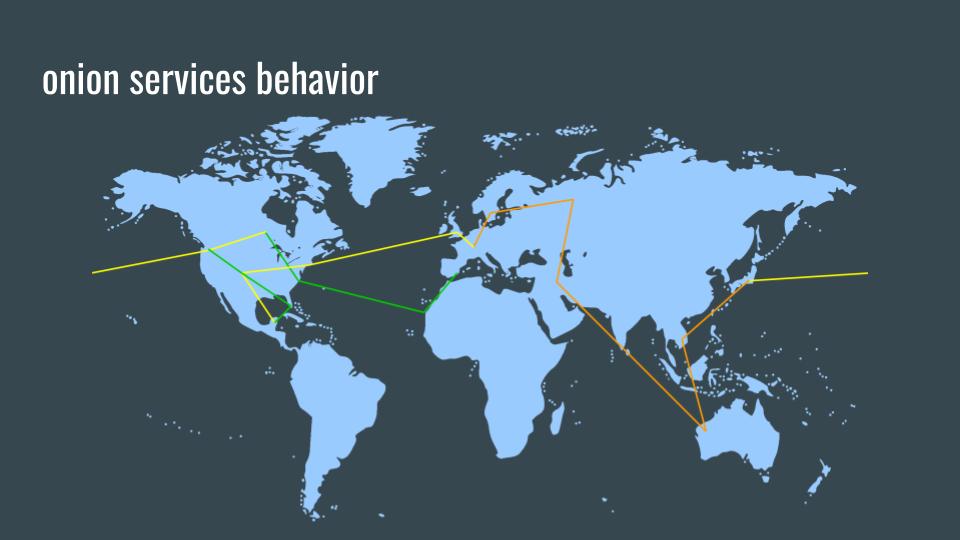
This simplified example of a client accessing an Onion service demonstrates the complexity and importance of Onion services. Because both the client and the server makes independent Tor circuits, both maintain anonymity while also providing end-to-end encryption.
Tor browser

Tor Browser, when juxtaposed to normal Web browsers, has significant advantages when the goal is to minimize identity exposure and the effects of Web tracking. Browser plug-ins cannot accomplish these privacy-focused goals, and many of these problems are identity-divulging browser features that advertising agencies always exploit.
If you are brand new to Tor, or generally need assistance with using a personal computer, these step-by-step guides are perfect for Tor Browser installation and basic use.
EFF SSD: How to: Use Tor for Windows
EFF SSD: How to: Use Tor for macOS
Onion services hosting
If you are interested in learning about or advocating for the use of Onion services, these are some useful resources.
Tor Project: Onion Services
Tor applications

This is a list of Tor related software applications for different platforms. It is not an exhaustive list, and in my talk I briefly described the purpose of each one.
Questions and feedback

Please email me with any questions or constructive feedback at yawnbox@disobey.net.